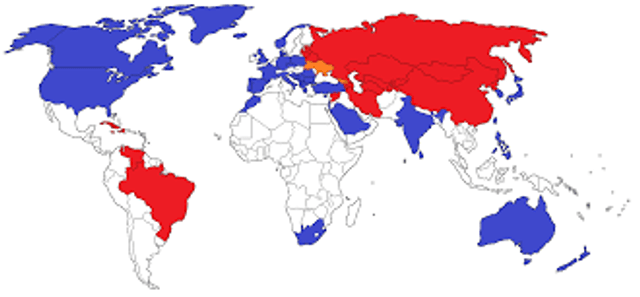
If it seems like there’s more security breaches than ever in just the last month, you’re not wrong. Long story short, Russia attacks Ukraine, anonymous hackers around the world support Ukraine and attack Russia via the Internet. Russia retaliates. The key here is to understand that every nation-state has a collection of “secret” security flaws […]
Here is a one-year look-back on the ever-changing cyber-security landscape broken out by type of attack and industry. The solid yellow bars are industries which are consistently under heavy attack year over year. The yellow totals are “new” industries, (i.e. whose score has risen to 3 or above in the last year). Please note that […]
We’ve all heard the stories about cyber criminals dumping thumb drives loaded with malicious code in employee parking lots waiting for one to be picked up and plugged into a work computer – it’s gotten to the point where it’s a TV show trope! And yes, of course, one certainly hopes your staff would be […]
Eight of the HPE 1910 Series switches employ Gigabit Ethernet technology and the other five employ Fast Ethernet Technology. Ethernet is a link-layer protocol that controls the movement of data throughout a network. Layer 1 is the physical layer of connections in the network, and the Data-Link layer is Layer 2 in the Open Systems […]
Why Multi-Factor Authentication (MFA) Is Just the Beginning It is true that implementing MFA in any form is much better than not having it, just like having better locks at your place of business, but there is a widely-touted statistic that is extremely mis-leading. A few years ago Microsoft released a paper indicating that 99% […]